cPanel is a Unix based fully featured popular web based hosting account control panel that helps webmasters to manage their domains through a web browser. The latest version of cPanel & WHM is 11.34, which is vulnerable to multiple cross site scripting.
During my bug hunting process, today I (Christy Philip Mathew) discovered some serious XSS vulnerabilities in official cPanel, WHM. It also impact on the latest version of software.
This week, Rafay Baloch (Pakistani white hat hacker) also discovered another reflective cross site scripting vulnerability in cPanel at manage.html.
The interesting part would be the whole demonstration I done with the Official cPanel Demo located athttp://cpanel.net/demo/ location, can be accessed via demo user & password provided by cPanel website itself i.e. http://demo.cpanel.net:2086/login/?user=demo&pass=demo
These vulnerabilities actually affect the logged in users. Proof of Concept and screenshots are as shown below:
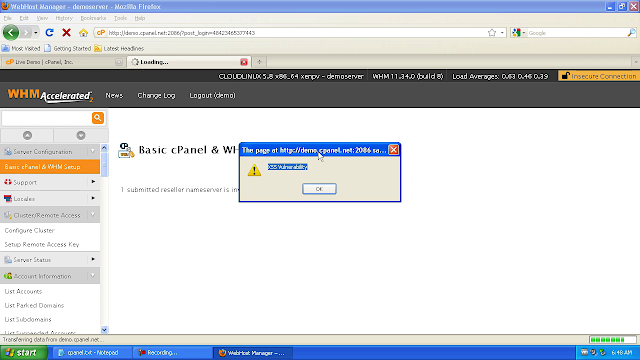
Cross Site scripting in Official WHM
- Login to WHM via : http://demo.cpanel.net:2086/login/?user=demo&pass=demo
- In left panel, click 'Server Configuration' and then 'Basic cPanel & WHM Setup' and new page will ask user to fill 4 Nameservers values regarding domain.
- Enter alert JavaScript in any of these four text boxes, as shown below and Submit
Cross Site scripting in Official cPanel
- Access the Official Cpanel Demo at http://x3demob.cpx3demo.com:2082/login/?user=x3demob&pass=x3demob
- Once logged in , access Bandwidth Transfer Detail (detailbw.html), and inject JavaScript in parameter "domain" or one can access this URL.
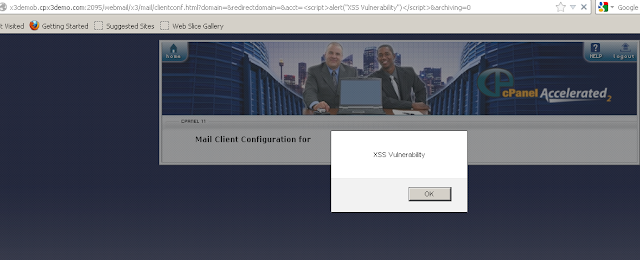
Cross Site scripting in WebMail server
- Similar way, access demo Webmail via URL : http://x3demob.cpx3demo.com:2082/xferwebmail/
- Once logged in XSS Vulnerable URL is : Click Here
- Here on page clientconf.html , the parameter "acct" is not filtered properly , as shown
More Details
- Product: Cpanel & WHM
- Security-Risk: High
- Remote-Exploit: yes
- Vendor-URL: http://www.cpanel.net
- Affected Products: Cpanel's Latest Version
- Solution: Proper input sanitisation.
- Discovered by: Christy Philip Mathew, Security researcher @ The Hacker News





It's hard to come by well-informed people for this subject, however, you sound like you know what you're talkіng about!
Τhanκѕ
Αlso vіѕit mу web sіte: sketchers sale
Here is my website - vacuums for hardwood floors
I do not knoω ωhеther it's just me or if perhaps everyone else experiencing problems with your blog. It seems like some of the written text within your posts are running off the screen. Can someone else please provide feedback and let me know if this is happening to them as well? This might be a issue with my browser because I've had this happen befοrе.
Thank you
my site :: ways to get more instagram followers
Thanks for one's marvelous posting! I actually enjoyed reading it, you will be a great author. I will remember to bookmark your blog and will eventually come back in the foreseeable future. I want to encourage you to definitely continue your great posts, have a nice evening!
Also visit my web blog - pikavippi
Look at my web blog pikavippi
I lіκe the valuable informatіon уou providе іn your articles.
I will boοkmarκ your blog and cheсk аgain hеre rеgularly.
I'm quite certain I will learn lots of new stuff right here! Best of luck for the next!
My site :: instagram folowers
Also see my site: get twitter followers fast
Hurrah, that's what I was exploring for, what a information! present here at this weblog, thanks admin of this web page.
Feel free to visit my page :: targeted twitter followers
My website - how to build followers on twitter
I read this paгagraph cοmρletelу concerning the differenсe
of newest and ρreνious technologiеs, it's awesome article.
Here is my blog post - http://followersempire.com/
Feel free to surf my website ; 10000 twitter followers