When we login into a website, we normally proceed by submitting our username and password. Then the server checks its database to match this information and if it finds it, sends a 'cookie' (a small piece of data) and stores into the user's web browser.
Usually websites encrypt the cookies containing the initial login but most of the time, everything else is left un-encrypted. This leaves the cookie vulnerable to session hijacking attacks.
How to hijack:
Programmer Eric Buttler has come up with a firefox extension called Firesheep which does exactly this but only with the ease of a button click. Click "Start Capturing" and the app starts to eavesdrop for any un-encrypted cookie that it may find in the network.
Step 1: Install Firesheep from this link: http://codebutler.github.com/firesheep
Immediately after installation you will notice a new sidebar pop-up.
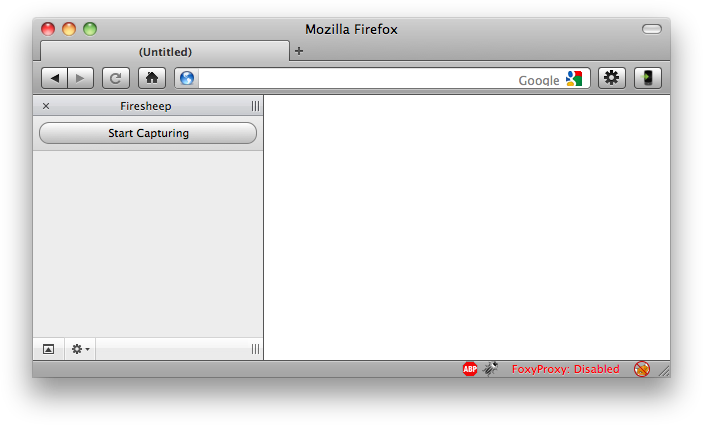
Step 2: Click on "Start Capturing" and within sometime you will be shocked to notice the number of unsecure cookies which it cracked.
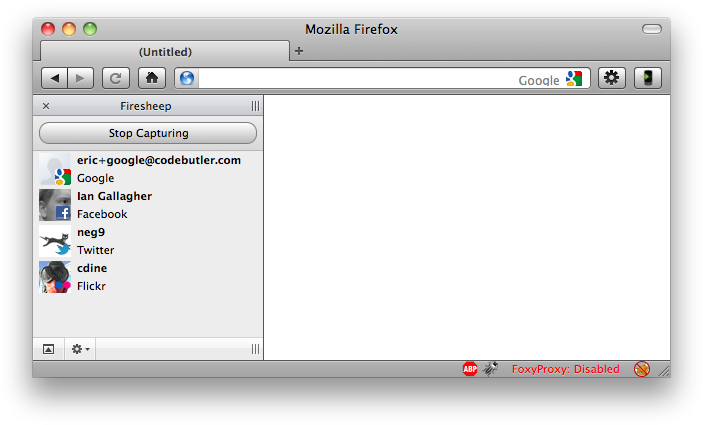
Step 3: Just as the list appears in your sidebar, you may click on any of the usernames and instantly you gain access to that website.

Even though it may sound cool to tryout yourself, just think how un-secure your own accounts are over a public network.
Follow these steps to protect yourself from the Firesheep Session Hijack Attack
1. Use http(secure) i.e., https://www.facebook.com to login.
This simple practice transmits your login information through an encrypted connection thus providing protection.
2. Another way is by using a VPN or Virtual Private Network.
Have you tried Firesheep? How was your experience? let us know. Share this post if you enjoyed reading.
Usually websites encrypt the cookies containing the initial login but most of the time, everything else is left un-encrypted. This leaves the cookie vulnerable to session hijacking attacks.
Session Hijack is when an attacker gets access to a user's cookie which allows them to do anything the real user can do on that specific website.In a wireless internet connection, like the WiFi, these cookies are basically shouted through the air making it even more vulnerable for the users and even easier for the attacker to hijack.
How to hijack:
Programmer Eric Buttler has come up with a firefox extension called Firesheep which does exactly this but only with the ease of a button click. Click "Start Capturing" and the app starts to eavesdrop for any un-encrypted cookie that it may find in the network.
Step 1: Install Firesheep from this link: http://codebutler.github.com/firesheep
Immediately after installation you will notice a new sidebar pop-up.

Step 2: Click on "Start Capturing" and within sometime you will be shocked to notice the number of unsecure cookies which it cracked.

Step 3: Just as the list appears in your sidebar, you may click on any of the usernames and instantly you gain access to that website.

Even though it may sound cool to tryout yourself, just think how un-secure your own accounts are over a public network.
Follow these steps to protect yourself from the Firesheep Session Hijack Attack
1. Use http(secure) i.e., https://www.facebook.com to login.
This simple practice transmits your login information through an encrypted connection thus providing protection.
2. Another way is by using a VPN or Virtual Private Network.
Have you tried Firesheep? How was your experience? let us know. Share this post if you enjoyed reading.



